Coprocessor: Trustless Computation Framework
2024-02-22
TL;DR
Phala Network introduces a decentralized, trustless framework for coprocessor computing, essential for advancing web3 applications. By utilizing Phat Contracts, Phala enables off-chain heavy computations with secure, hardware-based mechanisms and cryptographic proofs for verifiable task execution. This approach allows developers to access powerful coprocessor computing resources without compromising on decentralization. Phala addresses key challenges in the web3 ecosystem by trustlessly harnessing community-sourced coprocessor power and providing a computing service accessible to blockchain developers. Key innovations include a blockchain-TEE hybrid system for security and reliability, hierarchical key management for privacy preservation, and supply-end tokenomics to incentivize quality contributions. These elements collectively enhance the security, efficiency, and accessibility of decentralized computing, positioning Phala as a leader in integrating blockchain and TEE technologies for the web3 space.
Introduction to Coprocessor Computation
Phala Network introduces a decentralized, trustless coprocessor computing framework pivotal for advancing web3 applications. Leveraging Phat Contracts, it offers an innovative solution for executing heavy coprocessor computations off-chain, while ensuring seamless integration and enhanced functionality for dApps. The platform's coprocessor compute services rely on secure, hardware-based mechanisms and cryptographic proofs, ensuring verifiable and faithful execution of tasks. This enables developers to harness robust coprocessor computational capabilities without sacrificing web3's decentralization principles. By democratizing coprocessor compute resources, Phala stands as a foundational technology for next-generation dApp development.
Coprocessor Computation Power Management
Phala Network stands at the forefront of blockchain and TEE integration, offering a robust solution to web3's computing challenges. Through its innovative system design, hierarchical key management, and strategic tokenomics, Phala ensures the confidentiality, integrity, and availability of decentralized computing resources. As the first to implement such a comprehensive approach, Phala Network not only advances the security and efficiency of decentralized computing but also sets a new standard for trustless, community-powered web3 services.
Phala's primary goal is to establish a decentralized and trustless coprocessor computing network tailored for the web3 ecosystem. This mission hinges on addressing two critical challenges:
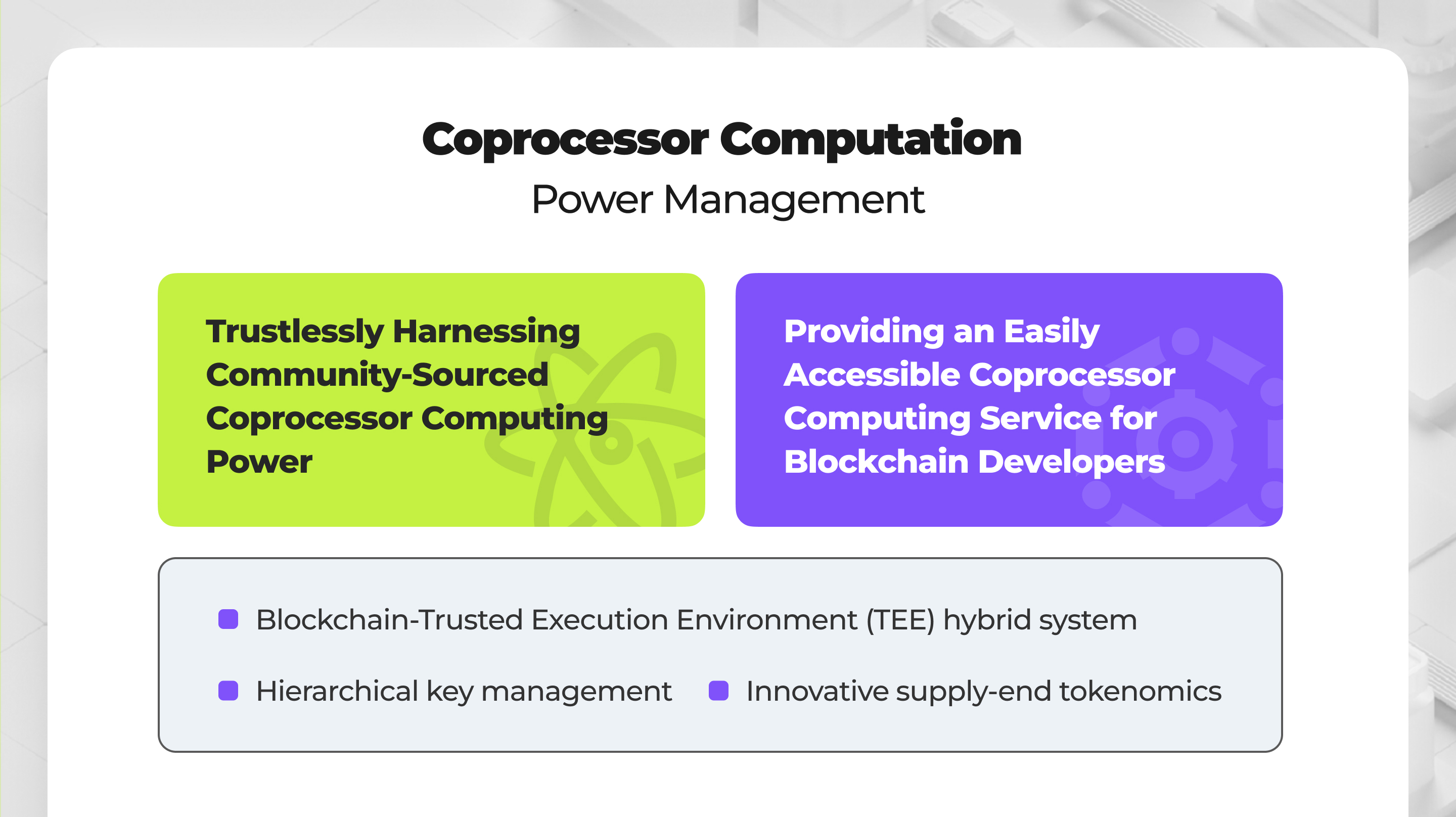
- Trustlessly Harnessing Community-Sourced Coprocessor Computing Power
- Providing an Easily Accessible Coprocessor Computing Service for Blockchain Developers
Phala Network's strategy involves a blend of technology and innovation, notably through a blockchain-Trusted Execution Environment (TEE) hybrid system, hierarchical key management, and innovative supply-end tokenomics.
These elements work together to provide a secure, efficient, and accessible computing service.
Blockchain-TEE Hybrid System: Ensuring Security and Reliability
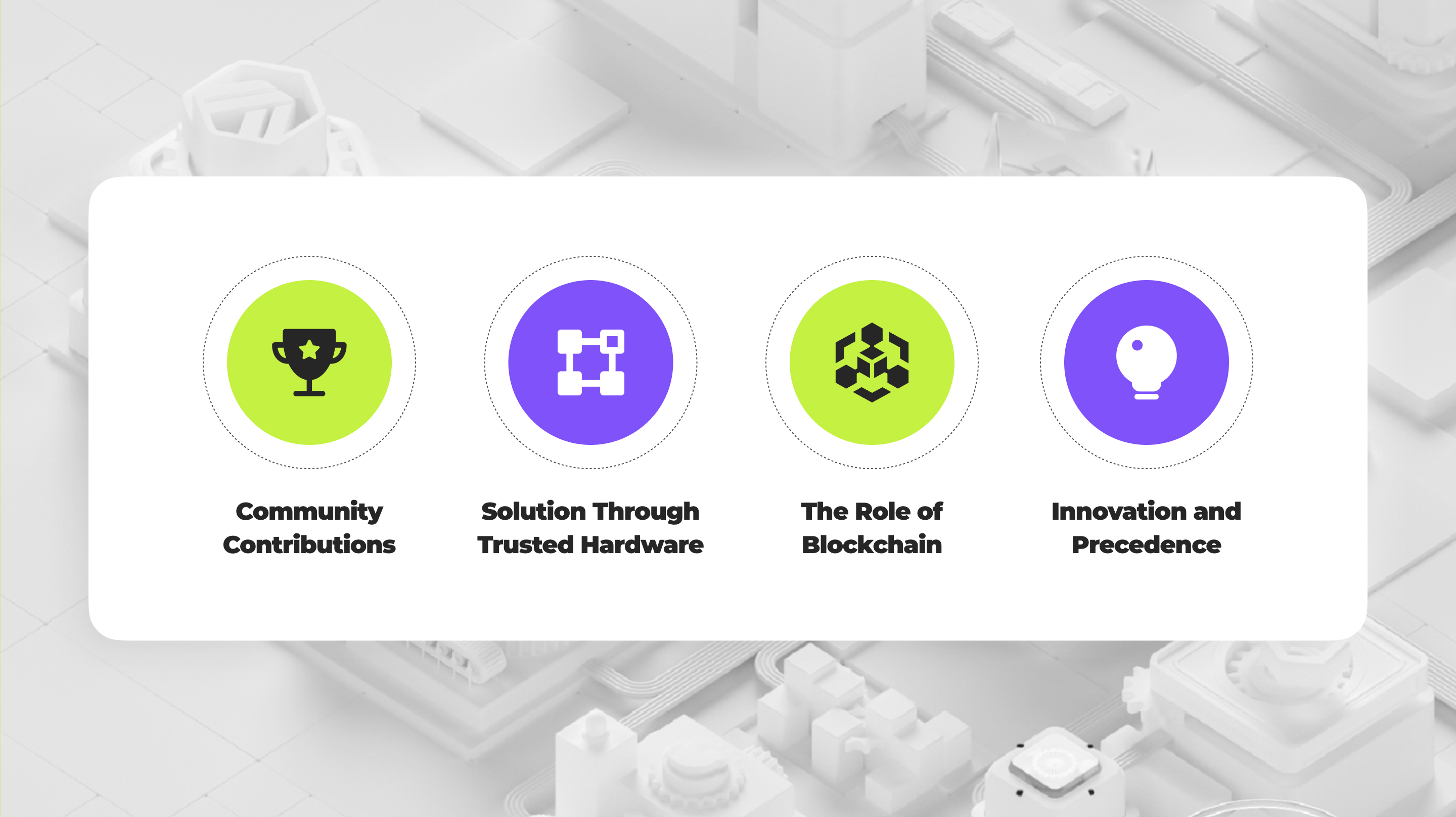
- Community Contributions: Phala leverages the power of community-contributed computing resources, facing the challenge of maintaining trust amidst potential malicious activities by hardware operators. This includes preventing the exposure of confidential program data or manipulation of execution results.
- Solution Through Trusted Hardware: The adoption of Trusted Execution Environment (TEE) technology ensures confidentiality and execution integrity, even in the face of malicious operators. TEEs, however, do not address the issue of availability—the risk of data loss due to server disconnections during execution.
- The Role of Blockchain: To combat this, Phala integrates blockchain technology, storing program codes and historical inputs securely. TEE workers operate statelessly, accessing and executing programs based on blockchain data, ensuring program state continuity.
- Innovation and Precedence: This model is inspired by the Ekiden paper and has been instrumental in the development of the Oasis Network.
Hierarchical Key Management: Assuring Privacy Always
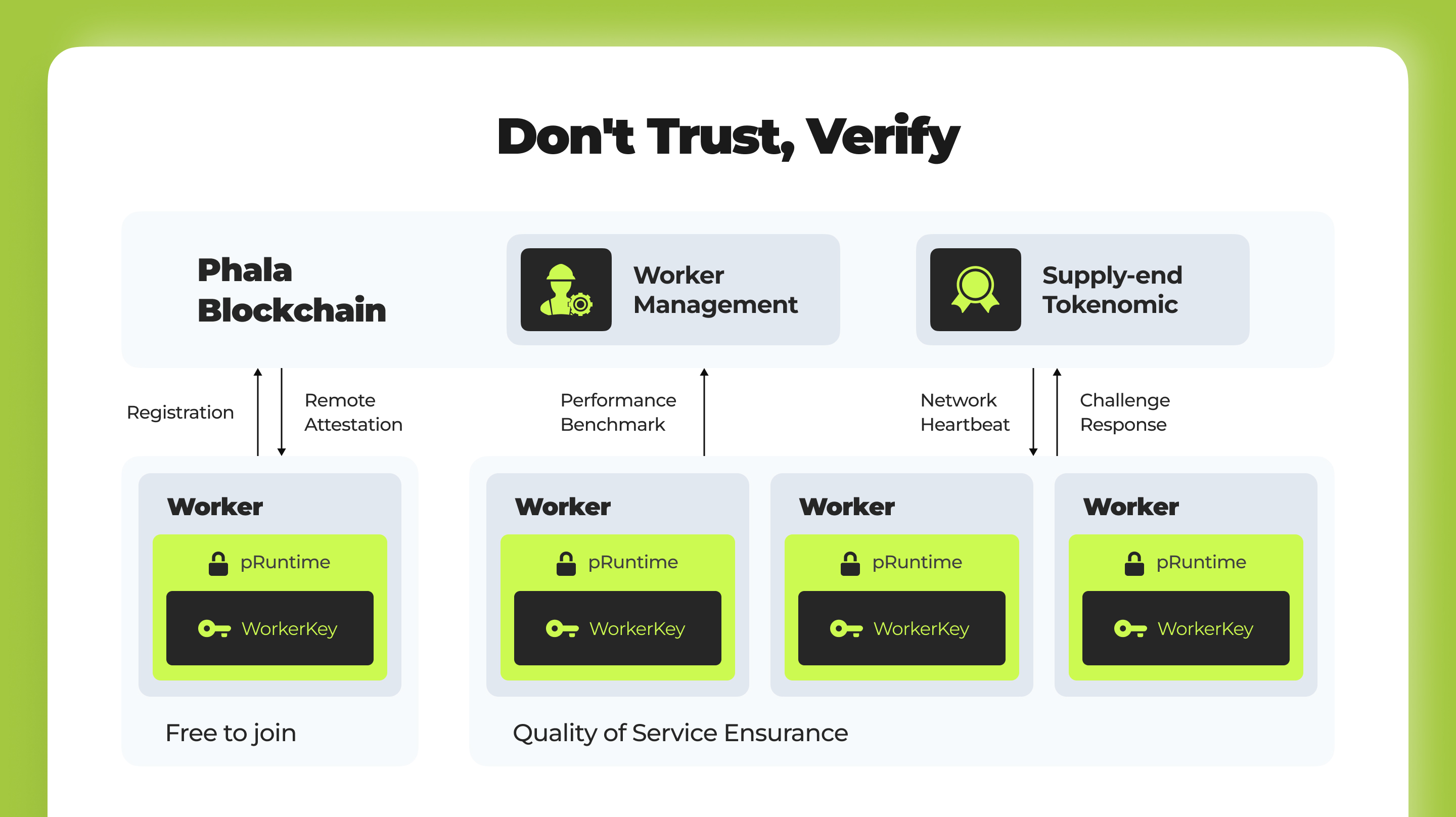
- Enhancing Confidentiality: Despite TEE's privacy assurances, the public nature of blockchain can compromise code and input confidentiality. Phala's solution involves exclusive secret keys within TEEs for encrypting and decrypting program data, preserving privacy.
- Mitigating Risks with Hierarchical Keys: Addressing vulnerabilities seen in systems like the Secret Network, Phala introduces a hierarchical key management system to prevent total network compromise from the breach of a single worker.
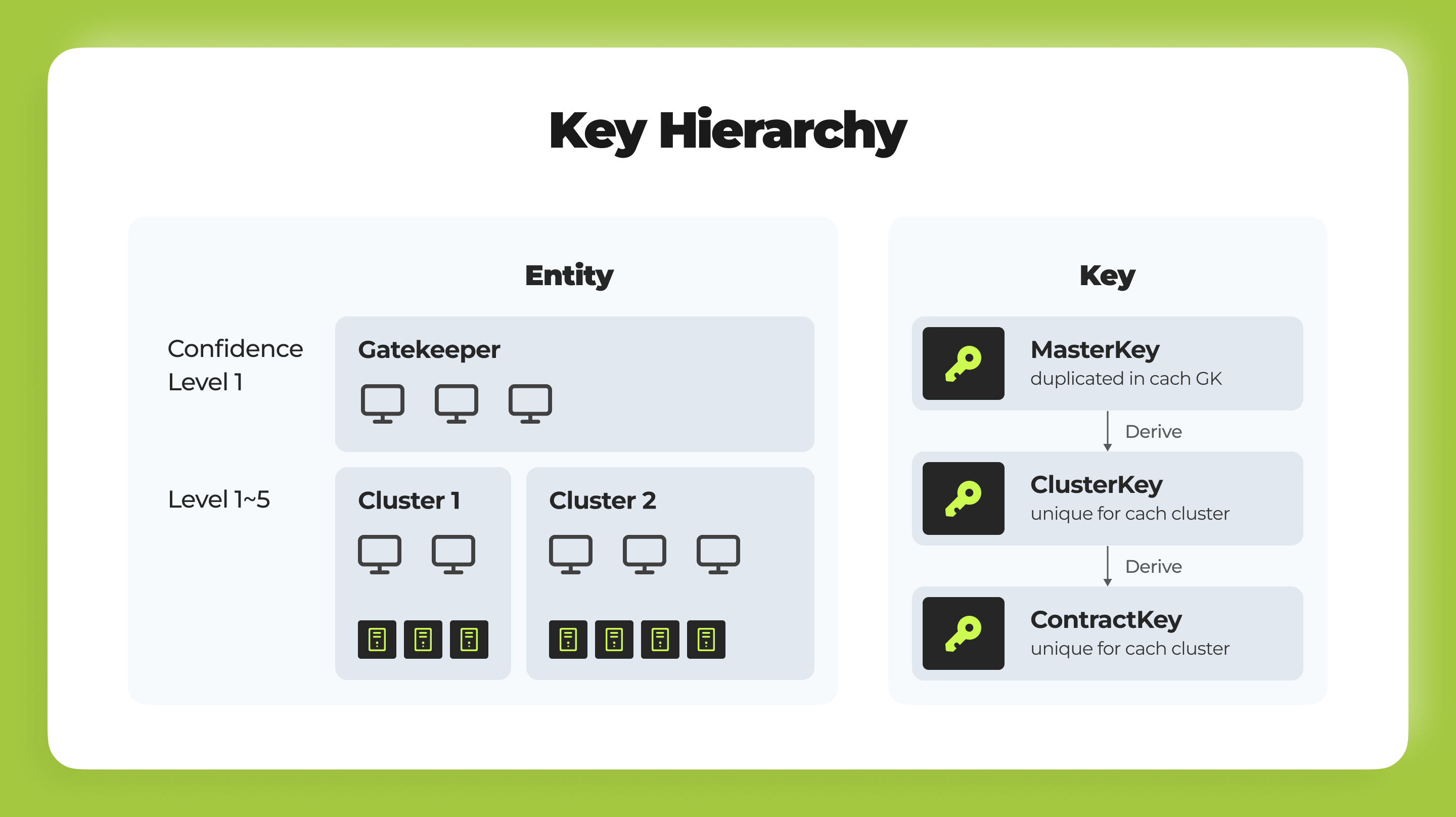
- Gatekeepers and Clusters: Distinguished by their robustness, select TEE workers act as Gatekeepers, safeguarding the master key. This key management structure minimizes potential damage, confining it to cluster levels in case of a compromise.
Supply-end Tokenomics: Driving Quality and Participation
- Encouraging Quality Contributions: Beyond security, Phala's tokenomics model incentivizes hardware owners to provide superior computing and network services, enhancing the overall quality and reliability of the Phala Network.
For further deep dive into the technical workings of Coprocessor Computation visit here.
Conclusion
Phala Network stands as a trailblazer in web3 technology, introducing a trustless and decentralized coprocessor computing framework that revolutionizes off-chain computations. Utilizing Phat Contracts, Phala enables developers to tap into advanced coprocessor capabilities without compromising decentralization's core values. Its innovative integration of a blockchain-TEE hybrid system, hierarchical key management, and supply-end tokenomics addresses the challenges of secure, efficient, and accessible decentralized computing head-on. This strategic approach not only elevates Phala as a key player in the web3 space but also underpins the future development of decentralized applications (dApps). As Phala continues to drive forward the web3 ecosystem, its commitment to enhancing security, privacy, and developer accessibility paves the way for a new wave of technological advancements, making it a foundational force in shaping the decentralized digital landscape.